- Choose FOUR(4) protocols and discuss its details and importance in network security.Research how they aid network security.
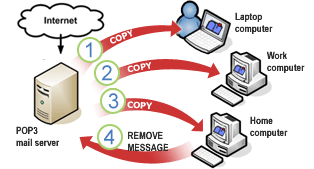
- POP3
-It stands for Post Office Protocol
-Allow you to download email message on your local computer
-Emails are stored on the server
-Sent messages are stored on the server
-Message can be synced and accessed across multiple devices
-Allow you to download email message on your local computer
-Emails are stored on the server
-Sent messages are stored on the server
-Message can be synced and accessed across multiple devices
Importance:
-It use to build a communication channel between an email client and server.
How?
-When a user checks for new email,the client will connect to the POP3 server.The email client then supplies its username and password to the server for authentication.
-It use to build a communication channel between an email client and server.
How?
-When a user checks for new email,the client will connect to the POP3 server.The email client then supplies its username and password to the server for authentication.
- DHCP
-It stand for Dynamic Host Configuration Protocol
-It is a client/server protocol that automatically provides an Internet Protocol (IP) host with its IP address and other related configuration information such as the subnet mask and default gateway.
-DHCP server automatically assigns an IP address and other information to each host on the network so they can communicate efficiently with other endpoints.
Importance:
-DHCP server dynamically assigns an IP address and other network configuration parameters to each devices on a network so they can communicate with other IP networks.
-It is a client/server protocol that automatically provides an Internet Protocol (IP) host with its IP address and other related configuration information such as the subnet mask and default gateway.
-DHCP server automatically assigns an IP address and other information to each host on the network so they can communicate efficiently with other endpoints.
Importance:
-DHCP server dynamically assigns an IP address and other network configuration parameters to each devices on a network so they can communicate with other IP networks.
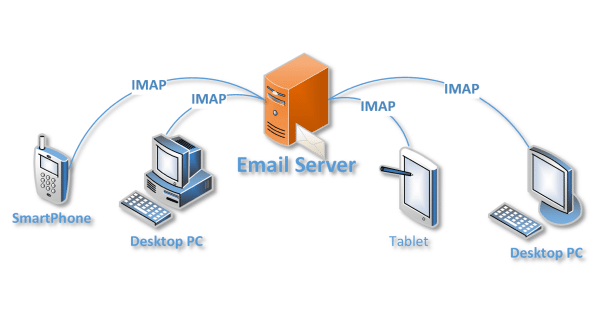
- IMAP
-It stands for Internet Messaging Access Protocol
-It is an internet standard that describes a protocol for retrieving messages from an email server
-When you read an email message ,you aren't actually downloading or storing it on your computer;instead you're reading it from email service.
Importance:
-It allow users to sync emails between multiple devices.
-It is an internet standard that describes a protocol for retrieving messages from an email server
-When you read an email message ,you aren't actually downloading or storing it on your computer;instead you're reading it from email service.
Importance:
-It allow users to sync emails between multiple devices.
- IPSEC
-IPsec stand for Internet Protocol Security
-It is a suite of protocols that secure network communication across IP networks.
-It provides security services for IP network traffic such as encrypting sensitive data, authentication, protection against replay and data confidentiality.
Importance:
-The data sent over the internet and private networks includes passwords.
How?
-It provide security for routers sending routing data across the public internet.